| assets | ||
| pkg | ||
| CODE_OF_CONDUCT.md | ||
| go.mod | ||
| go.sum | ||
| README.md | ||
PacketBreeze
PacketBreeze is an utility tool built for analysing and classifing packets by looking at packet headers.
Primary design goals:
PacketBreeze aims to:
- Classify packets and flows as benign or malicious with high true positives (TP) and low false positives (FP).
- Use the labeled data to reduce amount of traffic requiring deeper analysis.
Additionally, PacketBreeze also categorizes packets into flows and shows a rich ensemble of flow data and statistics.
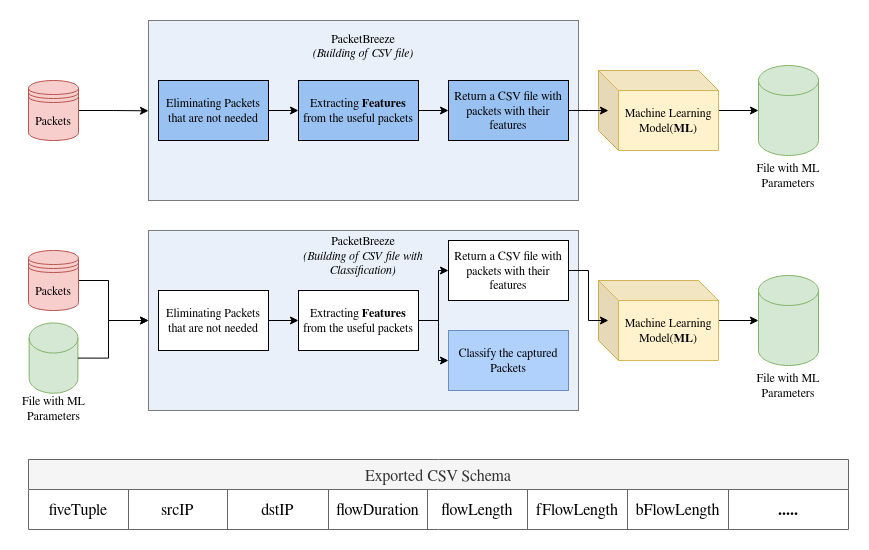 |
|---|
| PacketBreeze takes packets and returns file with statistics of flows. |
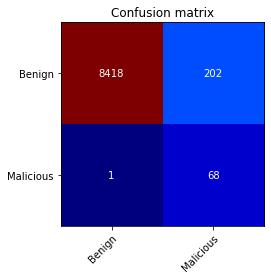 |
|---|
| Packetbreeze's output shown in a confusion matrix. |
When to use Packetbreeze
Use PacketBreeze if you wish to build and operate machine-learning models on network packet data.
Quick Start
Start by cloning the project: link
Build the binary:
foo@bar:~$ go build -o packetbreeze
Run the Binary:
foo@bar:~$ ./packetbreeze -ifLiveCapture=true -fname=webgoat -maxNumPackets=40000000 -ifLocalIPKnown false
Offline analysis of the PCAP packets
Requirements
Go Python Requirements in File
Who uses PacketBreeze?
-
One can use PacketBreeze to label the network packets using ML before deep analysis. Thus resulting in faster analysis overall.
-
Overall the target users for this project are intermediate network analyst, and network engineers.
Get in touch
Thank you for using PacketBreeze
Community contributions are always welcome through GitHub Issues and Pull Requests.
Developers
Arman Singh Kshatri 221020412
Swastika Satya 221020453