 |
|:--:|
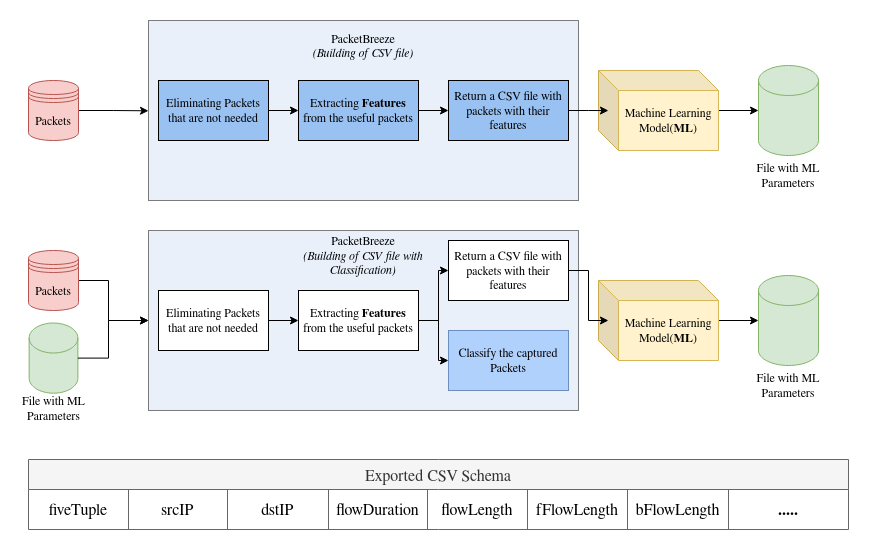
| *PacketBreeze takes packets and returns file with statistics of flows.* |
|
|
|:--:|
| *PacketBreeze takes packets and returns file with statistics of flows.* |
| 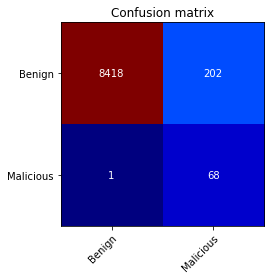 |:--:|
| *Packetbreeze's output shown in a confusion matrix.* |
## When to use Packetbreeze
Use PacketBreeze if you wish to build and operate machine-learning models on network packet data.
## Quick Start
Start by cloning the project: [link](https://git.weirdnatto.in/Unic-X/PacketBreeze.git)
Build the binary:
```console
foo@bar:~$ go build -o packetbreeze
```
Run the Binary:
```console
foo@bar:~$ ./packetbreeze -ifLiveCapture=true -fname=webgoat -maxNumPackets=40000000 -ifLocalIPKnown false
```
|:--:|
| *Packetbreeze's output shown in a confusion matrix.* |
## When to use Packetbreeze
Use PacketBreeze if you wish to build and operate machine-learning models on network packet data.
## Quick Start
Start by cloning the project: [link](https://git.weirdnatto.in/Unic-X/PacketBreeze.git)
Build the binary:
```console
foo@bar:~$ go build -o packetbreeze
```
Run the Binary:
```console
foo@bar:~$ ./packetbreeze -ifLiveCapture=true -fname=webgoat -maxNumPackets=40000000 -ifLocalIPKnown false
```
Offline analysis of the PCAP packets
--- ### Requirements Go Python Requirements in [File](assets/requirements.txt) ## Who uses PacketBreeze? * One can use PacketBreeze to label the network packets using ML before deep analysis. Thus resulting in faster analysis overall. * Overall the target users for this project are intermediate network analyst, and network engineers. ## Get in touch Thank you for using PacketBreeze Community contributions are always welcome through GitHub Issues and Pull Requests. ## Developers Arman Singh Kshatri `221020412` Swastika Satya `221020453`